Network Penetration Testing
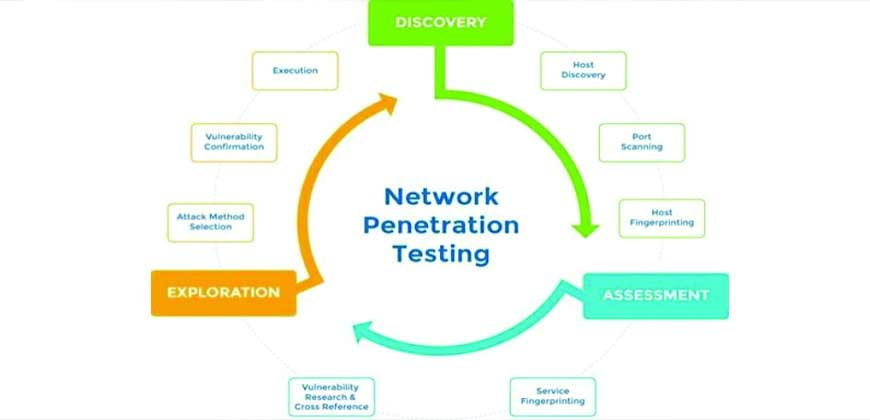
Network Penetration Testing
Organizations unaware of the hacker’s tools and approach fall prey to attacks compromising their systems. Hence, the best way for an organization to ensure that their infrastructure is secure is to employ security analysts to break their systems and notify them such that, they can avoid or mitigate the impact of such attacks, if exploited. This approach of testing your environment in the shoes of a hacker to assess the security posture is called Penetration Testing and these hackers who work hand-in-hand with the organizations to enhance their security are called white hat hackers or ethical hackers.
Network Penetration Test aims to identify vulnerabilities and risks in the network which may impact the Confidentiality, Integrity, and Availability (CIA) triad of data by simulating a real-world attack.
CYBERTEK’S NETWORK PENETRATION TESTING SERVICES
Types of Network Penetration Testing:
External Penetration Testing: It is conducted on external or public facing network to identify vulnerabilities that are visible to outsiders at large. It is done from any remote location over the internet without any explicit access permissions to the organization’s network.
Internal Penetration Testing: It is conducted on the internal network to identify vulnerabilities that are visible to potential insiders, contractors, partners with malicious intent. It is done at the vicinity of organization’s network with access permissions given to the attacker to show what risk is posed to information systems by organization’s employees, contractors and guests.
OUR APPROACH
Network Penetration Testing engagement constitutes our security testers to perform information gathering on systems in scope to identify services and functions which may be vulnerable, followed by Vulnerability detection phase which involves discovering vulnerabilities that affect the targets in scope. Then, we have the Attack/Exploitation phase where the targets are actively attacked to compromise, and finally in the Reporting phase where the discovered vulnerabilities are reported in a comprehensive and easily understandable manner. We require explicit permission from our clients to perform Penetration Testing.
Benefits:
- Proof of exploited videos and screen shots
- Increase the effectiveness of the security controls
- False positive elimination through manual verification
- Simulate as a hacker and provide a ‘Hacker’s eye-view’
- As Security test consultants we are Certified Ethical Hackers (CEH)
- Possess expertise in both open-source and commercial tools used for security testing
- Test in line with industry standards such as the SANS and Open-Source Security Testing Methodology Manual (OSSTMM)
What We Deliver:
We provide a detailed report after completion of the Penetration Testing. The report highlights the weaknesses in the system that affects the availability, reliability, and integrity of information assets. It also provides the solutions for covering each identified risk. The report contains the following:
- Categorization of weaknesses based on risk level
- Solution for discovered vulnerabilities
- Details of security holes discovered
Copyright© . CYBERTEK All right reserved.
