VAPT-Service

VAPT-Service
Why Security Assessments Are Essential
Nearly every product deals with critical enterprise data or sensitive personal information such as credit card numbers, social security numbers, private social user data or commercial secrets. A major flaw in a system or application can expose this protected information to a malicious hacker, resulting in financial damage, loss of reputation and disruption to business functions.
What’s more, in highly regulated industries like finance, healthcare or the public sector, ensuring the safety of your product is a principal requirement outlined in standards and regulations, including PCI DSS, HIPAA, CCHIT and many other mandatory standards. Complying with these is essential for every player in those industries.
Cybertek Security Services
Cybertek offers its clients a vulnerability assessment service, which is a comprehensive evaluation of a system for exposed vulnerabilities without their direct exploitation. Cost effective, regular vulnerability assessments can be a useful tool in staying up-to-date when it comes to security.
An application-level vulnerability assessment is a perfect fit for products during the late development stages before they reach production. It can be effectively completed in a test environment and help to make your product secure in time for release. For released applications, both vulnerability assessments and penetration testing can help ensure maximum security at all times.
Cybertek performs vulnerability assessments in accordance with “best-in-class” practices as defined by ISECOM's Open Source Security Testing Methodology Manual (OSSTMM) and the Open Web Application Security Project (OWASP). Our experts use both automated tools and manual techniques to identify vulnerabilities that threaten to compromise the security of sensitive information protected by a client’s infrastructure, policies and processes.
As a result of the assessment, Cybertek provides a comprehensive report containing identified risks, security weaknesses and misconfigurations as well as specific, actionable steps to eliminate identified vulnerabilities and improve overall security.
Service Highlights
Vulnerability assessment can help:
- identify security issues before they can be exploited;
- improve productivity by avoiding application downtime;
- protect the integrity and confidentiality of sensitive enterprise data;
- ensure security in time for product release.
By taking preventive measures, you can ultimately save thousands of dollars in losses from compromised reputation, reduced customer confidence, business disruptions, lost productivity and more.
Typical Workflow
The workflow for vulnerability assessment involves the following stages:
The workflow is very similar to penetration testing, with the major difference concerning the process of discovering vulnerabilities. While penetration testing is a real world attack simulation, during vulnerability assessment our experts do not exploit any of the vulnerabilities found. The Cybertek team uses both automated tools and manual techniques only to discover existing vulnerabilities.
VAPT (Vulnerability Assessments and Penetration Test) are comprehensive services for security audit, security amendment, recommendation, security monitoring, risk analysis, forensic analysis, and penetration testing.
Vulnerability Assessments & Penetration Testing Work Flow

What Digital Group provides
The Digital Group provides efficient Vulnerability Assessment and Penetration Testing (VAPT) services. The various services performed by the Digital Group professionals are as follows:
- Application Penetration Testing Services
- Network Penetration Testing Services
- External infrastructure Penetration Testing
- Internal infrastructure appliance Penetration Testing
- Mobile Application & Penetration Testing
- Client side software Penetration Testing
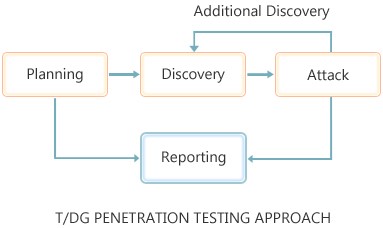
Penetration Testing Overview
- Source code review
- Functional Testing
- Performance Testing
- Memory Leakage Testing
- Usability Testing
- Authentication Testing
- Session Management
- Authorization Testing
- Data Validation Testing
Key Benefits
- VAPT services provided by the Digital Group incorporates comprehensive application evaluation rather than a single stand-alone test. It is a hybrid application testing process that involves two testing procedures.
- Testing of the IT systems at any point of time allows to mitigate risks in application development process, thus the cost involved in re-evaluation of the system is reduced.
- Using the Penetration Testing Approach gives an organization a more inclusive view of the threats encountered by various applications, systems, or networks.
- Our VAPT services enable various businesses to protect its systems and data from malicious attacks.
- Security measures for diverse applications and IT resources.
Copyright© . CYBERTEK All right reserved.
